ThreatLocker® Cyber Security Solution
ThreatLocker® is a leader in endpoint security technologies, providing enterprise-level cyber security tools to improve the security of servers and endpoints. The goal is to prevent attackers from gaining access to a company's network through undiscovered vulnerabilities in applications. The core of ThreatLocker solutions is the zero trust model.
- Unwanted software cannot run on your network, even if it has administrator rights.
- Stops known and unknown viruses, ransomware, and other malicious software.
- Enables the management and enforcement of policies for file sharing, USB device usage, and access to storage.
- Encrypts portable storage devices.
- Helps achieve compliance with information security standards and frameworks, such as CIS, NIST, HIPAA, ISO, etc.
Application Allowlisting
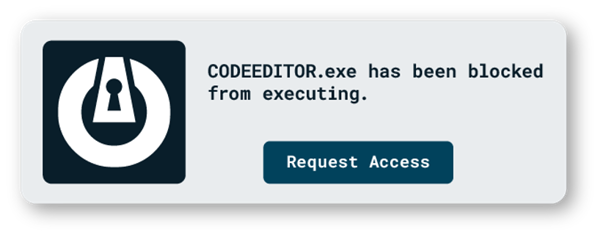
Application Allowlisting denies all applications from running except those that are explicitly allowed. This means unwanted software, including ransomware and other malware, will be denied by default.
Allow what you need and block everything else – including ransomware.
When the agent is first installed, it operates in Learning Mode. During this period, all applications and their dependencies found on the computer are cataloged and policies are created to permit them. After the learning, the IT administrators can review the list of applications, remove those that are not required, and secure the computer.
Once the computer is secured, any untrusted application, script, or library that tries to execute will be denied.
The user can easily make a request when launching a new application and add a reason why the particular application should be allowed. The IT administrator can allow, prohibit, or run the application in the ThreatLocker testing environment, where the reliability of the software, various parameters, and necessary settings for allowing or prohibiting the software can be controlled.
Stop malware attacks, prevent unauthorized application launches, and reduce cyber threats in your network.
Ringfencing™
Ringfencing™ controls what applications are able to do once they are running. By limiting what software can do, ThreatLocker® can reduce the likelihood of an exploit being successful, or an attacker weaponizing legitimate tools such as PowerShell.
- Stop fileless malware by limiting what applications are allowed to do.
- Granular application policies – stop applications from interacting with other applications, network resources, registry keys, files, and more.
- The average computer has over 500 applications and only a handful of those need to access your files. With Ringfencing™ you decide which applications need to see which files.
Limiting the activity of the applications reduces the likelihood of successful attacks. Even when the attacker uses permitted tools, such as PowerShell.
Under normal operations, all applications permitted on an endpoint or server are able to access all data that the operating user can access. This means if the application is compromised, the attacker can use the application to steal or encrypt files.
Ringfencing™ allows you to remove file access permissions for applications that do not need access and even remove network or registry permissions.
Elevation Control
Elevation Control enables users to run specific applications as a local administrator, even when they do not have local admin privileges.
- IT administrators are in the driving seat – they can control exactly what applications can run as a local admin without giving users local admin rights.
- Users can request permission to elevate applications and attach files and notes to support their requests.
- Enables to set duration for how long users are allowed access to specific applications by granting either temporary or permanent access.
- Secure application integration – Ringfencing™ ensures that once applications are elevated, users cannot jump to infiltrate connected applications within the network.
Storage Control
Storage Control provides policy-driven control over storage devices, whether the storage device is a local folder, a network share, or external storage such as a USB drive.
- Storage Control allows granular policies to be set. They could be as simple as blocking USB drives, or as detailed as blocking access to your backup share except when accessed by your backup application.
- Unified Audit provides a central log of all storage access by users on the network and those working remotely, right down to the files that were copied and the serial number of the device.
- The policies allow or deny access to storage based on user, time, application, and more.
Storage Control keeps an eye on who has access to the storage and where data can be stored.
Network Access Control (NAC)
ThreatLocker® NAC in an endpoint and server firewall that enables you to have total control over network traffic, which ultimately helps you to protect your devices.
- Ability to configure network access to endpoints using global and granular policies.
- Using custom-built policies, you can allow granular access based on IP aadress, specific keywords, agent authentication, or dynamic ACLs.
- The cloud-managed solution provides customers with a centralized view of endpoint policies and network traffic across your organization.
Users are not only working from the office but also remotely, meaning that the network we all utilize has quickly become the internet. This dissolution of the perimeter leaves devices and data vulnerable and exposed to cyber threats.
With ThreatLocker® NAC you can achieve that network traffic controls are in place to protect your devices and, by extension, your data.
ThreatLocker has a very high level and professional support with an average response time of less than 60 seconds. In addition, ThreatLocker has created a learning environment for its customers to get to know the application in detail.
BRS Networks Baltic is the only partner of ThreatLocker in Estonia. With our help, you can bring your company's cyber security to a level that protects against today's cyber threats.
Contact us Review other productsThreatLocker's website
This article is based on ThreatLocker's website and materials.
Discover how ThreatLocker can protect your business.